00 + Jahre
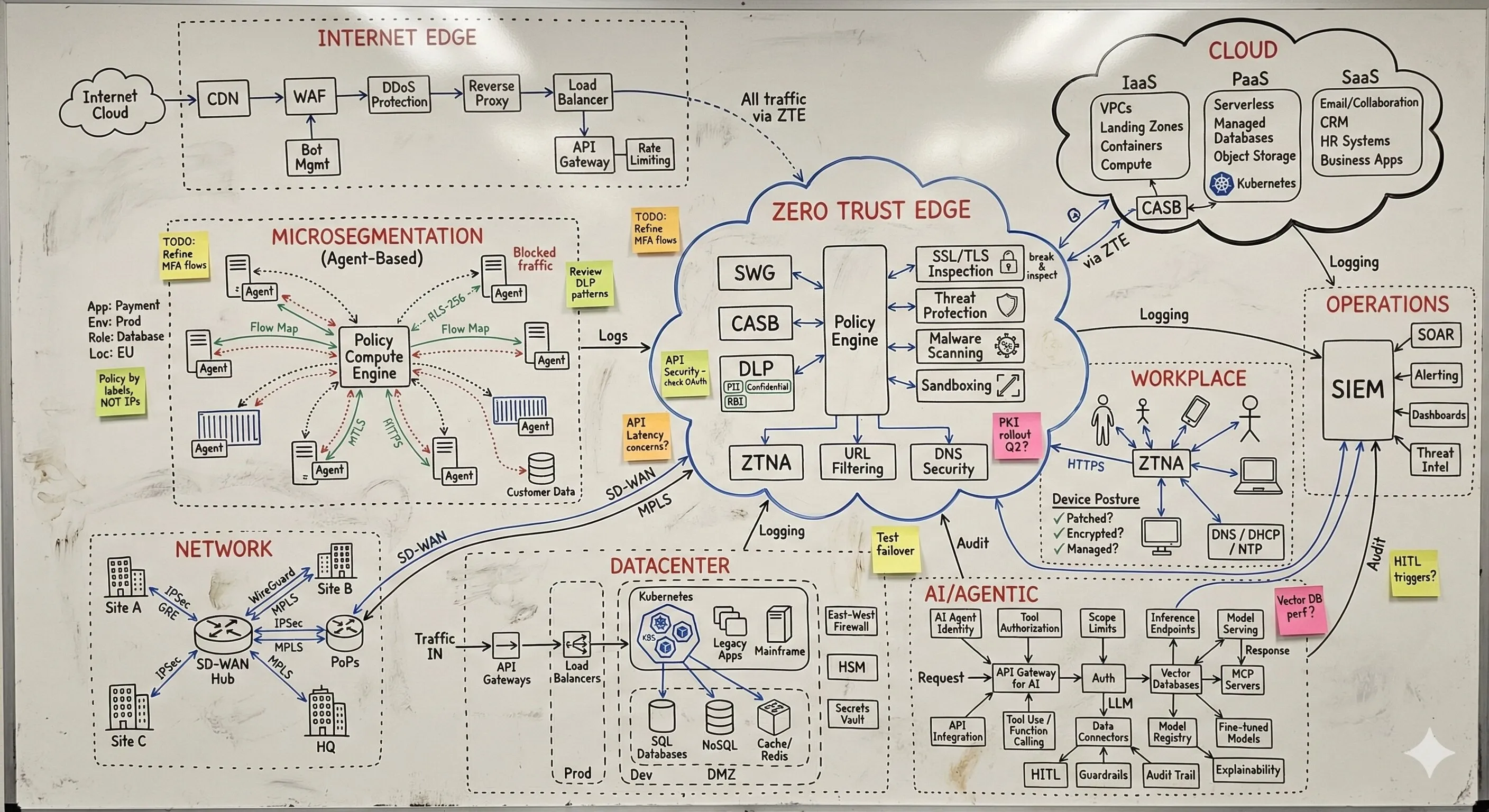
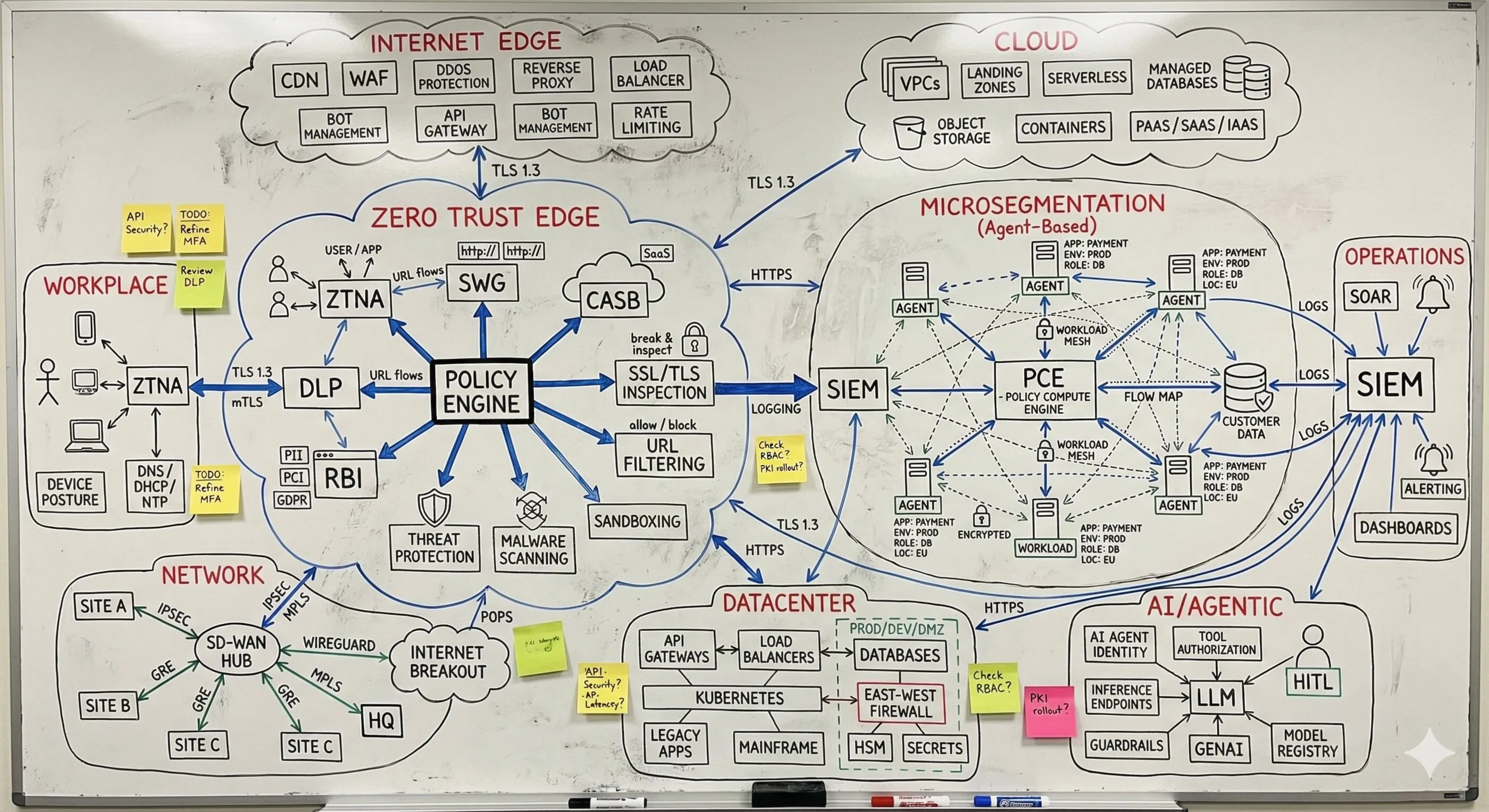
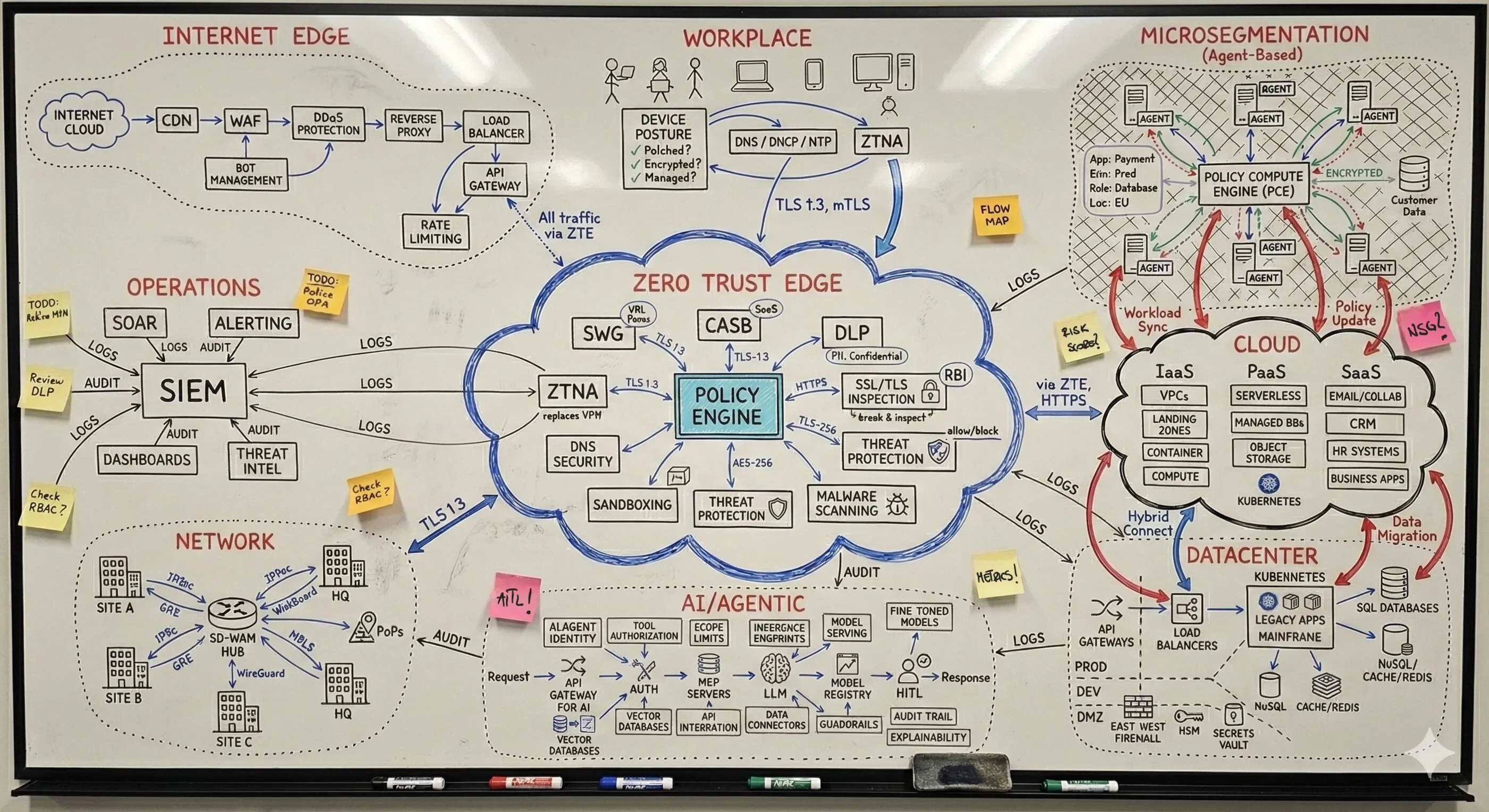
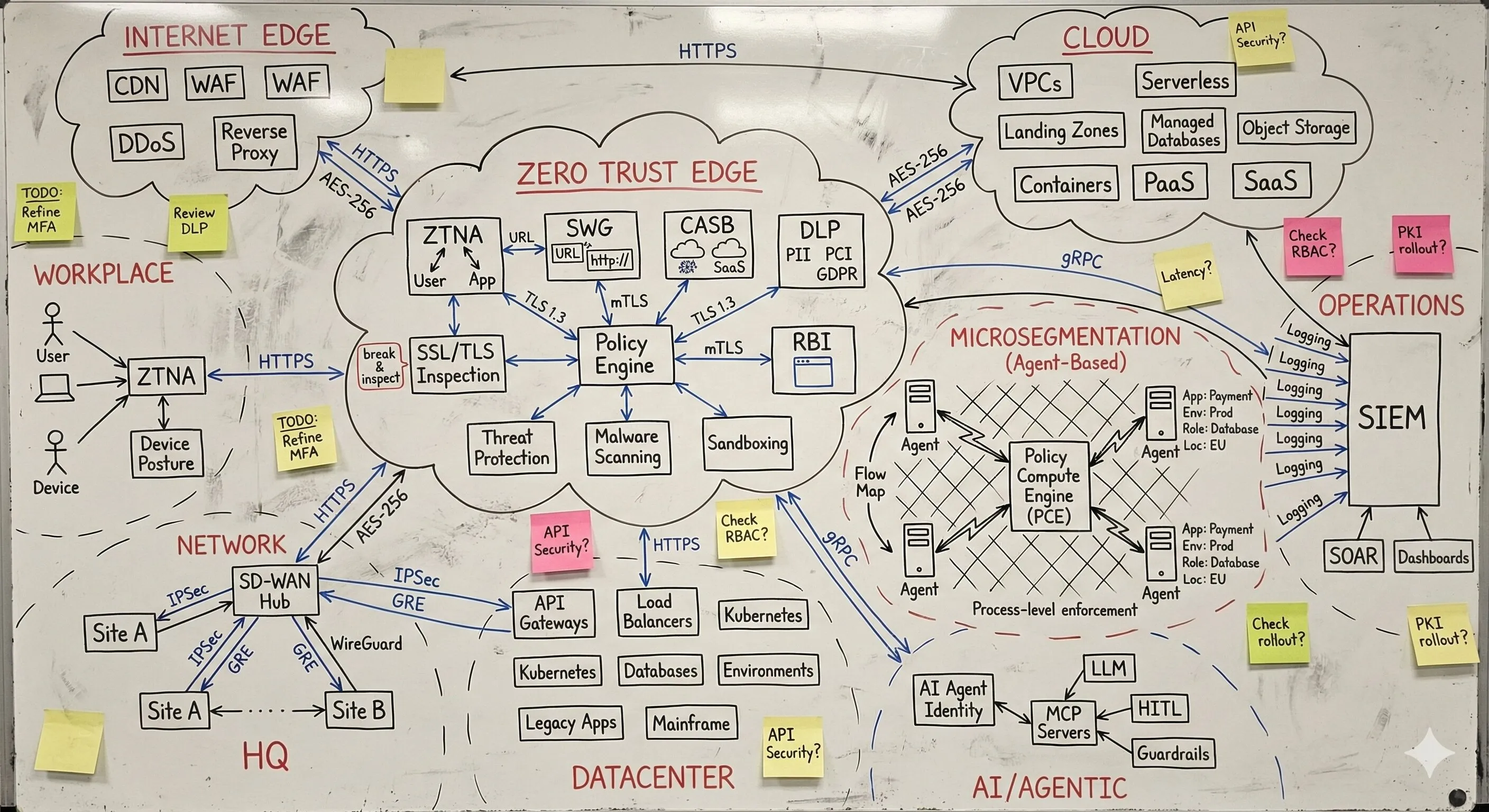
Unzusammenhängende Anforderungen, Produkte und Services in integrierte Architektur verwandeln, die auf Enterprise-Niveau funktioniert. Keine theoretischen Frameworks - funktionierende Systeme, bei denen Ausfälle keine Option sind. Von Umgebungen, die als nicht integrierbar galten, bis zu Infrastrukturen, die massgeschneiderte Ansätze erforderten. Dieselbe Integrations-Expertise, die Zero Trust für kritische nationale Infrastrukturen realisiert hat. Produktionssysteme statt Schubladendokumentation.
000 ° Sicht
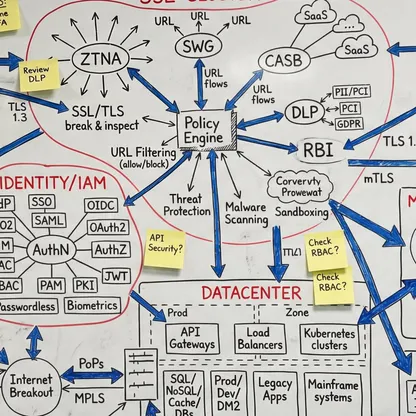
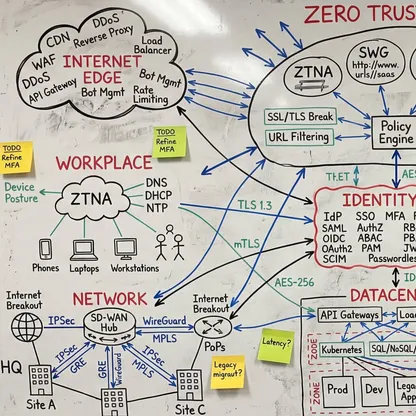
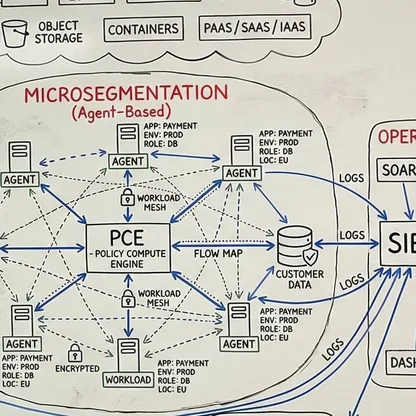
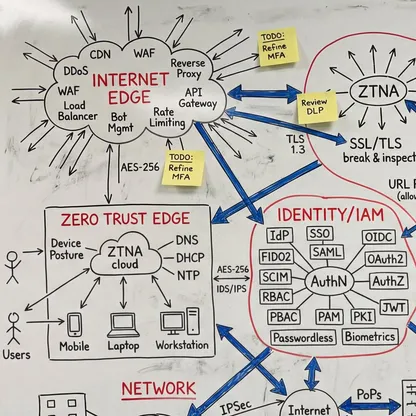
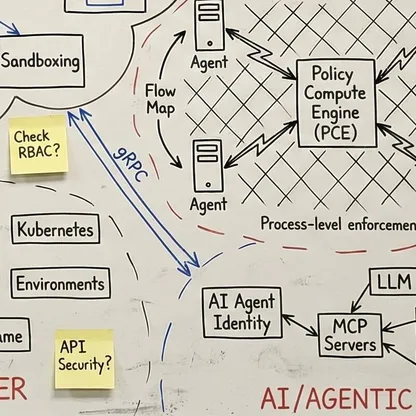
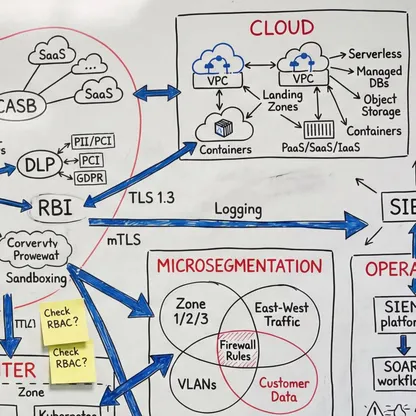
Ein vollständiges Verständnis Ihrer Umgebung - vom Edge bis zur Inferenz. Was unendlich komplex wirkt, wird beherrschbar, wenn jemand die Abhängigkeiten sichtbar macht. Mein Fokus liegt darauf, wie alles zusammenspielt: wo Übergaben scheitern, wo Richtlinien nicht sauber durchgesetzt werden und was nötig ist, damit die Sicherheitsschicht als ein kohärentes System funktioniert. Das ist der Unterschied zwischen Theorie und Produktionsarchitektur. Wenn Sie die Kette durchgängig verstehen, werden scheinbar unmögliche Probleme zu Engineering-Aufgaben mit klaren Lösungen.
0 Fabric
Eine integrierte Architektur, eine Policy-Fabric. Unabhängig von Ausgangslage, Reifegrad, Technologie-Stack oder organisationaler Komplexität ist das Ziel immer Konvergenz: Sicherheit, Konnektivität und KI arbeiten zusammen - statt an Schnittstellen auseinanderzufallen. Nicht Einzellösungen, die in den Lücken dazwischen versagen, sondern ein kohärenter Architekturrahmen, in dem die gesamte Schicht Entscheidungen gemeinsam durchsetzt: dieselbe Richtlinienentscheidung, überall, gleichzeitig. Das bedeutet Zero Trust, wenn es wirklich funktioniert.
Wie ich mit Ihnen arbeite
Bewerten - Wissen, wo Sie stehen
Jede Sicherheits-Transformation beginnt mit Klarheit. In strukturierten Workshops, technischen Analysen und Interviews mit Schlüsselpersonen bewerten wir Ihre Umgebung anhand bewährter Referenzmodelle.
Das Ergebnis ist ein priorisierter, umsetzbarer Fahrplan - abgestimmt auf Ihre technische Ausgangslage, regulatorische Anforderungen und betriebliche Rahmenbedingungen.

Architektur - Design für die Realität
Strategiepapiere sind nötig - aber sie sind noch keine Architektur. Gemeinsam übersetzen wir Ihr Sicherheitsziel in umsetzbare Entwürfe, die Ihre Anforderungen konkret abdecken.
Für komplexe Unternehmen löst diese Arbeit Herausforderungen, die Standardmodelle ignorieren: Einbindung von Altsystemen, Change Management und die Steuerung mehrjähriger Programme.

Begleiten - Expertenbegleitung
Die beste Architektur ist wertlos, wenn die Umsetzung scheitert. Mit Unterstützung bei der Anbieterauswahl, fachlicher Umsetzungsaufsicht und punktueller Beratung stellen wir sicher, dass Ihre Sicherheits-Transformation Ergebnisse liefert.
Das ist kein Projektmanagement. Es ist fachliche Steuerung, die Probleme erkennt, bevor sie zu Krisen werden.

Das bekommen Sie
Bereit, Ihre Sicherheitslage zu transformieren?
Ob Zero Trust Maturity Assessment, Review der Sicherheitsarchitektur oder Beratung zur Integration von KI in Ihre Security Operations - kontaktieren Sie mich direkt. Kein Verkaufsprozess. Keine Vorgespräche mit Junioren. Lassen Sie uns über Ihre Herausforderungen sprechen.
Nutzer
Kunden, Partner, Mitarbeitende
Endpunkte
Gesichert in Hybrid Multicloud Infrastruktur
Domains
Gesichert im gesamten Enterprise-Footprint